Continuation to the previous article I’m going to demonstrate how to create AWS EC2, ALB.
Backend.tf
terraform {
required_version = ">=0.13.0"
backend "s3" {
region = "eu-west-1"
profile = "default"
key = "terraformstatefile.tfstate"
bucket = "terraformstateinfo2020"
dynamodb_table = "terraformlocking"
}
}
Providers.tf
provider "aws" {
profile = var.profile
region = var.region
alias = "region"
}
variables.tf
variable "profile" {
type = string
default = "default"
}
variable "region" {
type = string
default = "eu-west-1"
}
variable "vpc_cidr" {
description = "Please entere cidr block"
type = string
default = "192.168.50.0/24"
}
variable "instance_type" {
description = "Please chose instance type"
type = string
default = "t3.medium"
}
variable "ec2_tags" {
type = map
default = {
Name = "appserver"
}
}
variable "ec2_amis" {
type = map
default = {
eu-west-1 = "ami-0fc970315c2d38f01"
eu-west-2 = "ami-098828924dc89ea4a"
}
}
variable "my_app_s3_bucket" {
type = string
default = "terraform-demo-202102171102"
}datasources.tf
# Declare the data source
data "aws_availability_zones" "azs" {
state = "available"
}vpc.tf
#Create VPC
resource "aws_vpc" "mydemodemo" {
provider = aws.region
cidr_block = var.vpc_cidr
instance_tenancy = "default"
enable_dns_support = true
enable_dns_hostnames = true
tags = {
Name = "mydemodemo",
Environment = terraform.workspace
}
}
publicsubnets.tf
locals {
az_names = data.aws_availability_zones.azs.names
public_sub_ids = aws_subnet.public.*.id
}
resource "aws_subnet" "public" {
count = length(slice(local.az_names, 0, 2))
vpc_id = aws_vpc.mydemodemo.id
cidr_block = cidrsubnet(var.vpc_cidr, 2, count.index)
availability_zone = local.az_names[count.index]
map_public_ip_on_launch = true
tags = {
Name = "PublicSubnet-${count.index + 1}"
}
}
# Internet Gateway Setup
resource "aws_internet_gateway" "igw" {
vpc_id = aws_vpc.mydemodemo.id
tags = {
Name = "mydemo-igw"
}
}
# Route tables for public subnets
resource "aws_route_table" "publicrt" {
vpc_id = aws_vpc.mydemodemo.id
route {
cidr_block = "0.0.0.0/0"
gateway_id = aws_internet_gateway.igw.id
}
tags = {
Name = "mydemopublicrt"
}
}
# Subents association for public subnets
resource "aws_route_table_association" "pub_subnet_association" {
count = length(slice(local.az_names, 0, 2))
subnet_id = aws_subnet.public.*.id[count.index]
route_table_id = aws_route_table.publicrt.id
}privatesubnets.tf
# Create private subnets
resource "aws_subnet" "private" {
count = length(slice(local.az_names, 0, 2))
vpc_id = aws_vpc.mydemodemo.id
cidr_block = cidrsubnet(var.vpc_cidr, 2, count.index + length(slice(local.az_names, 0, 2)))
availability_zone = local.az_names[count.index]
tags = {
Name = "PrivateSubnet-${count.index + 1}"
}
}
# Elastic IP for NAT Gateway
resource "aws_eip" "nat" {
vpc = true
}
# Create NAT Gateway for private subnets
resource "aws_nat_gateway" "ngw" {
# count = length(slice(local.az_names, 0, 2))
allocation_id = aws_eip.nat.id
subnet_id = aws_subnet.public.*.id[0]
tags = {
Name = "NatGateway"
}
}
output "nat_gateway_ip" {
value = aws_eip.nat.public_ip
}
# Route tables for private subnets
resource "aws_route_table" "privatert" {
vpc_id = aws_vpc.mydemodemo.id
route {
cidr_block = "0.0.0.0/0"
nat_gateway_id = aws_nat_gateway.ngw.id
}
tags = {
Name = "mydemoprivatert"
}
}
# Subents association for private subnets
resource "aws_route_table_association" "private_subnet_association" {
count = length(slice(local.az_names, 0, 2))
subnet_id = aws_subnet.private.*.id[count.index]
route_table_id = aws_route_table.privatert.id
}create iam roles , polcies for ec2 instance
data "template_file" "s3_ec2_policy" {
template = file("scripts/iam/ec2-policy.json")
vars = {
s3_bucket_arn = "arn:aws:s3:::${var.my_app_s3_bucket}/*"
}
}
resource "aws_iam_role_policy" "ec2_policy" {
name = "ec2_policy"
role = aws_iam_role.ec2_role.id
# Terraform's "jsonencode" function converts a
# Terraform expression result to valid JSON syntax.
policy = data.template_file.s3_ec2_policy.rendered
}
resource "aws_iam_role" "ec2_role" {
name = "ec2_role"
assume_role_policy = file("scripts/iam/ec2_assume_role.json")
}
# Attach role to EC2
resource "aws_iam_instance_profile" "ec2_profile" {
name = "ec2_profile"
role = aws_iam_role.ec2_role.name
}
ec2_assume_role.json
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"Service": "ec2.amazonaws.com"
},
"Action": "sts:AssumeRole"
}
]
}ec2-policy.json (This policy grants s3 list put and get, ec2 full access )
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "Stmt202102171510",
"Effect": "Allow",
"Action": [
"s3:ListStorageLensConfigurations",
"s3:ListAllMyBuckets",
"s3:ListJobs",
"ec2:*"
],
"Resource": "*"
},
{
"Sid": "Stmt202102171530",
"Effect": "Allow",
"Action": [
"s3:PutObject",
"s3:GetObject",
"s3:ListBucketMultipartUploads",
"s3:ListBucketVersions",
"s3:ListBucket",
"s3:ListMultipartUploadParts"
],
"Resource": [
"${s3_bucket_arn}",
"${s3_bucket_arn}/*"
]
}
]
}create s3 bucket
resource "aws_s3_bucket" "my_bucket" {
bucket = var.my_app_s3_bucket
acl = "private"
tags = {
Name = "My bucket"
Environment = terraform.workspace
}
}ec2-sg.tf
resource "aws_security_group" "ec2_sg" {
name = "ec2_sg"
description = "Allow inbound traffic for web applicaiton on ec2"
vpc_id = aws_vpc.mydemodemo.id
ingress { description = "web port"
from_port = 80 to_port = 80
protocol = "tcp" cidr_blocks = [aws_vpc.mydemodemo.cidr_block]
}
ingress {
description = "ssh port"
from_port = 22 to_port = 22
protocol = "tcp"
cidr_blocks = [aws_vpc.mydemodemo.cidr_block]
}
egress {
from_port = 0
to_port = 0
protocol = "-1"
cidr_blocks = ["0.0.0.0/0"]
}
tags = {
Name = "ec2_sg"
}
}ec2.tf
locals {
env_tag = {
Environment = terraform.workspace
}
tags = merge(var.ec2_tags, local.env_tag)
}
resource "aws_instance" "web" {
count = 2
ami = var.ec2_amis[var.region]
instance_type = var.instance_type
subnet_id = aws_subnet.private.*.id[count.index]
tags = var.ec2_tags
user_data = file("scripts/apache.sh")
iam_instance_profile = aws_iam_instance_profile.ec2_profile.name
vpc_security_group_ids = [aws_security_group.ec2_sg.id]
}The above script creates ec2 instance and attach iam role, and security group. Let us create application load balancer
alb.tf
# Create Target group
resource "aws_lb_target_group" "myapp" {
name = "myapp-lb-tg"
port = 80
protocol = "HTTP"
vpc_id = aws_vpc.mydemodemo.id
}
# Attach EC2 instances to traget group
resource "aws_lb_target_group_attachment" "myapp" {
count = 2
target_group_arn = aws_lb_target_group.myapp.arn
target_id = aws_instance.web.*.id[count.index]
port = 80
}
# Create ALB
resource "aws_lb" "myapp" {
name = "myapp-lb-tf"
internal = false
load_balancer_type = "application"
security_groups = [aws_security_group.alb_sg.id]
subnets = aws_subnet.public.*.id
enable_deletion_protection = true
tags = {
Environment = terraform.workspace
}
}
# Configure ALB Listerner
resource "aws_lb_listener" "myapp" {
load_balancer_arn = aws_lb.myapp.arn
port = "80"
protocol = "HTTP"
default_action {
type = "forward"
target_group_arn = aws_lb_target_group.myapp.arn
}
}Please note that this is just a demonstration of how to create EC2 and ALB using terraform and i’ve not created certificate for alb example here. You can create ssl cert and attach it to alb.
Now, let us do terraform plan
terraform plan
provider.aws.region
The region where AWS operations will take place. Examples
are us-east-1, us-west-2, etc.
Enter a value: eu-west-1
Refreshing Terraform state in-memory prior to plan...
The refreshed state will be used to calculate this plan, but will not be
persisted to local or remote state storage.
data.template_file.s3_ec2_policy: Refreshing state...
data.aws_availability_zones.azs: Refreshing state...
------------------------------------------------------------------------
An execution plan has been generated and is shown below.
Resource actions are indicated with the following symbols:
+ create
Terraform will perform the following actions:
# aws_eip.nat will be created
+ resource "aws_eip" "nat" {
+ allocation_id = (known after apply)
+ association_id = (known after apply)
+ customer_owned_ip = (known after apply)
+ domain = (known after apply)
+ id = (known after apply)
+ instance = (known after apply)
+ network_border_group = (known after apply)
+ network_interface = (known after apply)
+ private_dns = (known after apply)
+ private_ip = (known after apply)
+ public_dns = (known after apply)
+ public_ip = (known after apply)
+ public_ipv4_pool = (known after apply)
+ vpc = true
}
# aws_iam_instance_profile.ec2_profile will be created
+ resource "aws_iam_instance_profile" "ec2_profile" {
+ arn = (known after apply)
+ create_date = (known after apply)
+ id = (known after apply)
+ name = "ec2_profile"
+ path = "/"
+ role = "ec2_role"
+ unique_id = (known after apply)
}
# aws_iam_role.ec2_role will be created
+ resource "aws_iam_role" "ec2_role" {
+ arn = (known after apply)
+ assume_role_policy = jsonencode(
{
+ Statement = [
+ {
+ Action = "sts:AssumeRole"
+ Effect = "Allow"
+ Principal = {
+ Service = "ec2.amazonaws.com"
}
},
]
+ Version = "2012-10-17"
}
)
+ create_date = (known after apply)
+ force_detach_policies = false
+ id = (known after apply)
+ max_session_duration = 3600
+ name = "ec2_role"
+ path = "/"
+ unique_id = (known after apply)
}
# aws_iam_role_policy.ec2_policy will be created
+ resource "aws_iam_role_policy" "ec2_policy" {
+ id = (known after apply)
+ name = "ec2_policy"
+ policy = jsonencode(
{
+ Statement = [
+ {
+ Action = [
+ "s3:ListStorageLensConfigurations",
+ "s3:ListAllMyBuckets",
+ "s3:ListJobs",
+ "ec2:*",
]
+ Effect = "Allow"
+ Resource = "*"
+ Sid = "Stmt202102171510"
},
+ {
+ Action = [
+ "s3:PutObject",
+ "s3:GetObject",
+ "s3:ListBucketMultipartUploads",
+ "s3:ListBucketVersions",
+ "s3:ListBucket",
+ "s3:ListMultipartUploadParts",
]
+ Effect = "Allow"
+ Resource = [
+ "arn:aws:s3:::terraform-demo-202102171103/*",
+ "arn:aws:s3:::terraform-demo-202102171103/*/*",
]
+ Sid = "Stmt202102171530"
},
]
+ Version = "2012-10-17"
}
)
+ role = (known after apply)
}
# aws_instance.web[0] will be created
+ resource "aws_instance" "web" {
+ ami = "ami-0fc970315c2d38f01"
+ arn = (known after apply)
+ associate_public_ip_address = (known after apply)
+ availability_zone = (known after apply)
+ cpu_core_count = (known after apply)
+ cpu_threads_per_core = (known after apply)
+ get_password_data = false
+ host_id = (known after apply)
+ iam_instance_profile = "ec2_profile"
+ id = (known after apply)
+ instance_state = (known after apply)
+ instance_type = "t3.medium"
+ ipv6_address_count = (known after apply)
+ ipv6_addresses = (known after apply)
+ key_name = (known after apply)
+ outpost_arn = (known after apply)
+ password_data = (known after apply)
+ placement_group = (known after apply)
+ primary_network_interface_id = (known after apply)
+ private_dns = (known after apply)
+ private_ip = (known after apply)
+ public_dns = (known after apply)
+ public_ip = (known after apply)
+ secondary_private_ips = (known after apply)
+ security_groups = (known after apply)
+ source_dest_check = true
+ subnet_id = (known after apply)
+ tags = {
+ "Name" = "appserver"
}
+ tenancy = (known after apply)
+ user_data = "4cf0e018e9af98d1b7ebab63b0c032d4a207b7ef"
+ volume_tags = (known after apply)
+ vpc_security_group_ids = (known after apply)
+ ebs_block_device {
+ delete_on_termination = (known after apply)
+ device_name = (known after apply)
+ encrypted = (known after apply)
+ iops = (known after apply)
+ kms_key_id = (known after apply)
+ snapshot_id = (known after apply)
+ volume_id = (known after apply)
+ volume_size = (known after apply)
+ volume_type = (known after apply)
}
+ ephemeral_block_device {
+ device_name = (known after apply)
+ no_device = (known after apply)
+ virtual_name = (known after apply)
}
+ metadata_options {
+ http_endpoint = (known after apply)
+ http_put_response_hop_limit = (known after apply)
+ http_tokens = (known after apply)
}
+ network_interface {
+ delete_on_termination = (known after apply)
+ device_index = (known after apply)
+ network_interface_id = (known after apply)
}
+ root_block_device {
+ delete_on_termination = (known after apply)
+ device_name = (known after apply)
+ encrypted = (known after apply)
+ iops = (known after apply)
+ kms_key_id = (known after apply)
+ volume_id = (known after apply)
+ volume_size = (known after apply)
+ volume_type = (known after apply)
}
}
# aws_instance.web[1] will be created
+ resource "aws_instance" "web" {
+ ami = "ami-0fc970315c2d38f01"
+ arn = (known after apply)
+ associate_public_ip_address = (known after apply)
+ availability_zone = (known after apply)
+ cpu_core_count = (known after apply)
+ cpu_threads_per_core = (known after apply)
+ get_password_data = false
+ host_id = (known after apply)
+ iam_instance_profile = "ec2_profile"
+ id = (known after apply)
+ instance_state = (known after apply)
+ instance_type = "t3.medium"
+ ipv6_address_count = (known after apply)
+ ipv6_addresses = (known after apply)
+ key_name = (known after apply)
+ outpost_arn = (known after apply)
+ password_data = (known after apply)
+ placement_group = (known after apply)
+ primary_network_interface_id = (known after apply)
+ private_dns = (known after apply)
+ private_ip = (known after apply)
+ public_dns = (known after apply)
+ public_ip = (known after apply)
+ secondary_private_ips = (known after apply)
+ security_groups = (known after apply)
+ source_dest_check = true
+ subnet_id = (known after apply)
+ tags = {
+ "Name" = "appserver"
}
+ tenancy = (known after apply)
+ user_data = "4cf0e018e9af98d1b7ebab63b0c032d4a207b7ef"
+ volume_tags = (known after apply)
+ vpc_security_group_ids = (known after apply)
+ ebs_block_device {
+ delete_on_termination = (known after apply)
+ device_name = (known after apply)
+ encrypted = (known after apply)
+ iops = (known after apply)
+ kms_key_id = (known after apply)
+ snapshot_id = (known after apply)
+ volume_id = (known after apply)
+ volume_size = (known after apply)
+ volume_type = (known after apply)
}
+ ephemeral_block_device {
+ device_name = (known after apply)
+ no_device = (known after apply)
+ virtual_name = (known after apply)
}
+ metadata_options {
+ http_endpoint = (known after apply)
+ http_put_response_hop_limit = (known after apply)
+ http_tokens = (known after apply)
}
+ network_interface {
+ delete_on_termination = (known after apply)
+ device_index = (known after apply)
+ network_interface_id = (known after apply)
}
+ root_block_device {
+ delete_on_termination = (known after apply)
+ device_name = (known after apply)
+ encrypted = (known after apply)
+ iops = (known after apply)
+ kms_key_id = (known after apply)
+ volume_id = (known after apply)
+ volume_size = (known after apply)
+ volume_type = (known after apply)
}
}
# aws_internet_gateway.igw will be created
+ resource "aws_internet_gateway" "igw" {
+ arn = (known after apply)
+ id = (known after apply)
+ owner_id = (known after apply)
+ tags = {
+ "Name" = "mydemo-igw"
}
+ vpc_id = (known after apply)
}
# aws_lb.myapp will be created
+ resource "aws_lb" "myapp" {
+ arn = (known after apply)
+ arn_suffix = (known after apply)
+ dns_name = (known after apply)
+ drop_invalid_header_fields = false
+ enable_deletion_protection = true
+ enable_http2 = true
+ id = (known after apply)
+ idle_timeout = 60
+ internal = false
+ ip_address_type = (known after apply)
+ load_balancer_type = "application"
+ name = "myapp-lb-tf"
+ security_groups = (known after apply)
+ subnets = (known after apply)
+ tags = {
+ "Environment" = "demo"
}
+ vpc_id = (known after apply)
+ zone_id = (known after apply)
+ subnet_mapping {
+ allocation_id = (known after apply)
+ outpost_id = (known after apply)
+ private_ipv4_address = (known after apply)
+ subnet_id = (known after apply)
}
}
# aws_lb_listener.myapp will be created
+ resource "aws_lb_listener" "myapp" {
+ arn = (known after apply)
+ id = (known after apply)
+ load_balancer_arn = (known after apply)
+ port = 80
+ protocol = "HTTP"
+ ssl_policy = (known after apply)
+ default_action {
+ order = (known after apply)
+ target_group_arn = (known after apply)
+ type = "forward"
}
}
# aws_lb_target_group.myapp will be created
+ resource "aws_lb_target_group" "myapp" {
+ arn = (known after apply)
+ arn_suffix = (known after apply)
+ deregistration_delay = 300
+ id = (known after apply)
+ lambda_multi_value_headers_enabled = false
+ load_balancing_algorithm_type = (known after apply)
+ name = "myapp-lb-tg"
+ port = 80
+ protocol = "HTTP"
+ proxy_protocol_v2 = false
+ slow_start = 0
+ target_type = "instance"
+ vpc_id = (known after apply)
+ health_check {
+ enabled = (known after apply)
+ healthy_threshold = (known after apply)
+ interval = (known after apply)
+ matcher = (known after apply)
+ path = (known after apply)
+ port = (known after apply)
+ protocol = (known after apply)
+ timeout = (known after apply)
+ unhealthy_threshold = (known after apply)
}
+ stickiness {
+ cookie_duration = (known after apply)
+ enabled = (known after apply)
+ type = (known after apply)
}
}
# aws_lb_target_group_attachment.myapp[0] will be created
+ resource "aws_lb_target_group_attachment" "myapp" {
+ id = (known after apply)
+ port = 80
+ target_group_arn = (known after apply)
+ target_id = (known after apply)
}
# aws_lb_target_group_attachment.myapp[1] will be created
+ resource "aws_lb_target_group_attachment" "myapp" {
+ id = (known after apply)
+ port = 80
+ target_group_arn = (known after apply)
+ target_id = (known after apply)
}
# aws_nat_gateway.ngw will be created
+ resource "aws_nat_gateway" "ngw" {
+ allocation_id = (known after apply)
+ id = (known after apply)
+ network_interface_id = (known after apply)
+ private_ip = (known after apply)
+ public_ip = (known after apply)
+ subnet_id = (known after apply)
+ tags = {
+ "Name" = "NatGateway"
}
}
# aws_route_table.privatert will be created
+ resource "aws_route_table" "privatert" {
+ id = (known after apply)
+ owner_id = (known after apply)
+ propagating_vgws = (known after apply)
+ route = [
+ {
+ cidr_block = "0.0.0.0/0"
+ egress_only_gateway_id = ""
+ gateway_id = ""
+ instance_id = ""
+ ipv6_cidr_block = ""
+ local_gateway_id = ""
+ nat_gateway_id = (known after apply)
+ network_interface_id = ""
+ transit_gateway_id = ""
+ vpc_endpoint_id = ""
+ vpc_peering_connection_id = ""
},
]
+ tags = {
+ "Name" = "mydemoprivatert"
}
+ vpc_id = (known after apply)
}
# aws_route_table.publicrt will be created
+ resource "aws_route_table" "publicrt" {
+ id = (known after apply)
+ owner_id = (known after apply)
+ propagating_vgws = (known after apply)
+ route = [
+ {
+ cidr_block = "0.0.0.0/0"
+ egress_only_gateway_id = ""
+ gateway_id = (known after apply)
+ instance_id = ""
+ ipv6_cidr_block = ""
+ local_gateway_id = ""
+ nat_gateway_id = ""
+ network_interface_id = ""
+ transit_gateway_id = ""
+ vpc_endpoint_id = ""
+ vpc_peering_connection_id = ""
},
]
+ tags = {
+ "Name" = "mydemopublicrt"
}
+ vpc_id = (known after apply)
}
# aws_route_table_association.private_subnet_association[0] will be created
+ resource "aws_route_table_association" "private_subnet_association" {
+ id = (known after apply)
+ route_table_id = (known after apply)
+ subnet_id = (known after apply)
}
# aws_route_table_association.private_subnet_association[1] will be created
+ resource "aws_route_table_association" "private_subnet_association" {
+ id = (known after apply)
+ route_table_id = (known after apply)
+ subnet_id = (known after apply)
}
# aws_route_table_association.pub_subnet_association[0] will be created
+ resource "aws_route_table_association" "pub_subnet_association" {
+ id = (known after apply)
+ route_table_id = (known after apply)
+ subnet_id = (known after apply)
}
# aws_route_table_association.pub_subnet_association[1] will be created
+ resource "aws_route_table_association" "pub_subnet_association" {
+ id = (known after apply)
+ route_table_id = (known after apply)
+ subnet_id = (known after apply)
}
# aws_s3_bucket.my_bucket will be created
+ resource "aws_s3_bucket" "my_bucket" {
+ acceleration_status = (known after apply)
+ acl = "private"
+ arn = (known after apply)
+ bucket = "terraform-demo-202102171103"
+ bucket_domain_name = (known after apply)
+ bucket_regional_domain_name = (known after apply)
+ force_destroy = false
+ hosted_zone_id = (known after apply)
+ id = (known after apply)
+ region = (known after apply)
+ request_payer = (known after apply)
+ tags = {
+ "Environment" = "demo"
+ "Name" = "My bucket"
}
+ website_domain = (known after apply)
+ website_endpoint = (known after apply)
+ versioning {
+ enabled = (known after apply)
+ mfa_delete = (known after apply)
}
}
# aws_security_group.alb_sg will be created
+ resource "aws_security_group" "alb_sg" {
+ arn = (known after apply)
+ description = "Allow inbound traffic for web applicaiton on ec2"
+ egress = (known after apply)
+ id = (known after apply)
+ ingress = [
+ {
+ cidr_blocks = [
+ "0.0.0.0/0",
]
+ description = "alb web port"
+ from_port = 80
+ ipv6_cidr_blocks = []
+ prefix_list_ids = []
+ protocol = "tcp"
+ security_groups = []
+ self = false
+ to_port = 80
},
]
+ name = "alb_sg"
+ owner_id = (known after apply)
+ revoke_rules_on_delete = false
+ tags = {
+ "Name" = "alb_sg"
}
+ vpc_id = (known after apply)
}
# aws_security_group.ec2_sg will be created
+ resource "aws_security_group" "ec2_sg" {
+ arn = (known after apply)
+ description = "Allow inbound traffic for web applicaiton on ec2"
+ egress = [
+ {
+ cidr_blocks = [
+ "0.0.0.0/0",
]
+ description = ""
+ from_port = 0
+ ipv6_cidr_blocks = []
+ prefix_list_ids = []
+ protocol = "-1"
+ security_groups = []
+ self = false
+ to_port = 0
},
]
+ id = (known after apply)
+ ingress = [
+ {
+ cidr_blocks = [
+ "192.168.50.0/24",
]
+ description = "ssh port"
+ from_port = 22
+ ipv6_cidr_blocks = []
+ prefix_list_ids = []
+ protocol = "tcp"
+ security_groups = []
+ self = false
+ to_port = 22
},
+ {
+ cidr_blocks = [
+ "192.168.50.0/24",
]
+ description = "web port"
+ from_port = 80
+ ipv6_cidr_blocks = []
+ prefix_list_ids = []
+ protocol = "tcp"
+ security_groups = []
+ self = false
+ to_port = 80
},
]
+ name = "ec2_sg"
+ owner_id = (known after apply)
+ revoke_rules_on_delete = false
+ tags = {
+ "Name" = "ec2_sg"
}
+ vpc_id = (known after apply)
}
# aws_subnet.private[0] will be created
+ resource "aws_subnet" "private" {
+ arn = (known after apply)
+ assign_ipv6_address_on_creation = false
+ availability_zone = "eu-west-1a"
+ availability_zone_id = (known after apply)
+ cidr_block = "192.168.50.128/26"
+ id = (known after apply)
+ ipv6_cidr_block_association_id = (known after apply)
+ map_public_ip_on_launch = false
+ owner_id = (known after apply)
+ tags = {
+ "Name" = "PrivateSubnet-1"
}
+ vpc_id = (known after apply)
}
# aws_subnet.private[1] will be created
+ resource "aws_subnet" "private" {
+ arn = (known after apply)
+ assign_ipv6_address_on_creation = false
+ availability_zone = "eu-west-1b"
+ availability_zone_id = (known after apply)
+ cidr_block = "192.168.50.192/26"
+ id = (known after apply)
+ ipv6_cidr_block_association_id = (known after apply)
+ map_public_ip_on_launch = false
+ owner_id = (known after apply)
+ tags = {
+ "Name" = "PrivateSubnet-2"
}
+ vpc_id = (known after apply)
}
# aws_subnet.public[0] will be created
+ resource "aws_subnet" "public" {
+ arn = (known after apply)
+ assign_ipv6_address_on_creation = false
+ availability_zone = "eu-west-1a"
+ availability_zone_id = (known after apply)
+ cidr_block = "192.168.50.0/26"
+ id = (known after apply)
+ ipv6_cidr_block_association_id = (known after apply)
+ map_public_ip_on_launch = true
+ owner_id = (known after apply)
+ tags = {
+ "Name" = "PublicSubnet-1"
}
+ vpc_id = (known after apply)
}
# aws_subnet.public[1] will be created
+ resource "aws_subnet" "public" {
+ arn = (known after apply)
+ assign_ipv6_address_on_creation = false
+ availability_zone = "eu-west-1b"
+ availability_zone_id = (known after apply)
+ cidr_block = "192.168.50.64/26"
+ id = (known after apply)
+ ipv6_cidr_block_association_id = (known after apply)
+ map_public_ip_on_launch = true
+ owner_id = (known after apply)
+ tags = {
+ "Name" = "PublicSubnet-2"
}
+ vpc_id = (known after apply)
}
# aws_vpc.mydemodemo will be created
+ resource "aws_vpc" "mydemodemo" {
+ arn = (known after apply)
+ assign_generated_ipv6_cidr_block = false
+ cidr_block = "192.168.50.0/24"
+ default_network_acl_id = (known after apply)
+ default_route_table_id = (known after apply)
+ default_security_group_id = (known after apply)
+ dhcp_options_id = (known after apply)
+ enable_classiclink = (known after apply)
+ enable_classiclink_dns_support = (known after apply)
+ enable_dns_hostnames = true
+ enable_dns_support = true
+ id = (known after apply)
+ instance_tenancy = "default"
+ ipv6_association_id = (known after apply)
+ ipv6_cidr_block = (known after apply)
+ main_route_table_id = (known after apply)
+ owner_id = (known after apply)
+ tags = {
+ "Environment" = "demo"
+ "Name" = "mydemodemo"
}
}
Plan: 27 to add, 0 to change, 0 to destroy.
Changes to Outputs:
+ nat_gateway_ip = (known after apply)
------------------------------------------------------------------------
Note: You didn't specify an "-out" parameter to save this plan, so Terraform
can't guarantee that exactly these actions will be performed if
"terraform apply" is subsequently run.If you can see that plan is creating ec2, ec2 roles, ec2 security groups, attaching ec2_role to ec2 instance, creating target groups, alb, listerners. Let us apply terraform


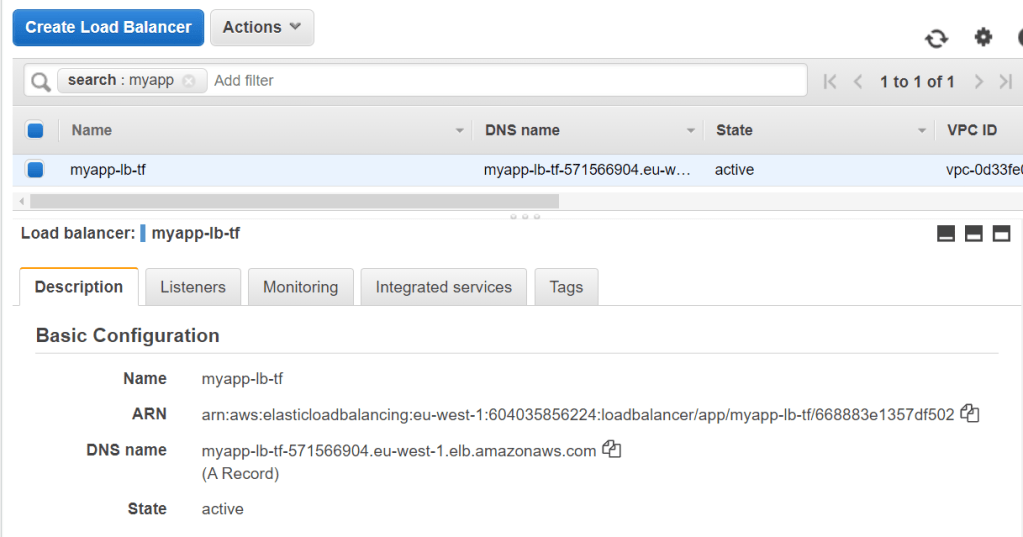
That’s it. if you see that the ec2 and alb’s are created. you can customize the script based on your requirement.
Hope you enjoyed the post.
Cheers
Ramasankar Molleti
